Exploring End-to-End Encryption in WebRTC
As developers of software solutions, it's crucial to integrate secure and reliable video conferencing into your applications. Whether you're building an event platform or telehealth service, protecting users' privacy and ensuring secure communication is paramount. This blog post will guide you through the concept of end-to-end encryption in WebRTC video conferencing, highlighting its benefits and differences from other encryption methods.
By understanding the advantages of E2EE, you'll be better equipped to implement secure video conferencing for your clients and users.
Table of Contents
- What is End-to-End Encryption?
- How Does End-to-End Encryption Work?
- Differences from Other Types of Encryption
- What Does E2EE Protect the User From?
- The Benefits of End-to-End Encrypted Video Conferencing
- Differences Between Symmetric and Asymmetric Encryption
- How does End-to-End Encryption for conference calls work in WebRTC
- Choosing the Right Video Conferencing API Provider
- How to enable End-to-End Encryption on Digital Samba
- Conclusion
What is end-to-end encryption?
End-to-end encryption refers to a secure method of communication that encrypts data at the sender's end and decrypts it only at the recipient's end. This ensures that only the intended recipients can access the sensitive data, including audio, video, and text messages exchanged during video conference calls.
This type of encryption provides a high level of security, as even if the message is intercepted or hacked, it will be unreadable to anyone who does not have the decryption key. End-to-end encryption is increasingly being adopted by conferencing service providers as a way to protect sensitive information and ensure user privacy.
How does end-to-end encryption (E2EE) work?
End-to-end encryption is a sophisticated method of communication that ensures the privacy and security of data exchanged between parties. To help developers understand E2EE's inner workings, let's break down the process step by step:
Key generation
Both the sender and recipient generate a pair of encryption keys: a public key for encryption and a private key for decryption. The public keys are exchanged between the parties, while the private keys remain confidential.
Secure key exchange
To establish a secure communication channel, the sender and recipient use a key exchange protocol, such as Diffie-Hellman, to generate a shared secret key. This secret key is derived from the sender's private key and the recipient's public key (or vice versa), ensuring that only the intended parties can derive the secret key.
Encryption
The sender uses the shared secret key to encrypt the data, including audio, video, and text messages, before transmission. This encryption process typically involves a symmetric encryption algorithm, such as AES, which provides a balance between speed and security.
Transmission
The encrypted data is transmitted over the network, safeguarded against unauthorised access and tampering. Even if an attacker manages to intercept the data, they will not be able to decrypt it without the shared secret key.
Decryption
Upon receiving the encrypted data, the recipient uses their private key and the sender's public key to derive the same shared secret key used for encryption. The recipient then uses this secret key to decrypt the data, restoring it to its original form.
Secure communication
As the encryption and decryption process is repeated for every message exchanged between the sender and recipient, the entire communication remains secure and private, protected from eavesdroppers and potential attackers.
By employing this end-to-end encryption process, developers can ensure that only the intended recipients can access sensitive data exchanged during video conference calls. This robust method of communication is vital for maintaining privacy and data security in an increasingly digital world.

Differences from other types of encryption
End-to-end encryption (E2EE) provides a higher level of security compared to other types of encryption because the message is encrypted and decrypted only on the sender's and receiver's devices. This means that even if the communication platform is compromised, the message remains secure.
- Compared to E2EE, Transport Layer Security (TLS) encryption, also known as server-side encryption, only encrypts data in transit between the user's device and the server. This means that the server can access the decrypted data, leaving it vulnerable to data breaches or surveillance.
- Similarly, Secure Real-time Transport Protocol (SRTP) encryption, a commonly used encryption protocol for real-time communication, encrypts media streams between users but not the signalling information, such as metadata or call setup information. This makes SRTP vulnerable to certain types of attacks, such as traffic analysis.
- In contrast to the types mentioned above, E2EE provides forward secrecy, meaning that even if the attacker obtains the encryption keys, they cannot decrypt past communications. This provides an additional layer of protection for users' sensitive information in transit.
What does E2EE protect the user from?
End-to-end encryption provides a high level of security for user messages in video conference calls by protecting against a variety of threats, including:
Interception of messages
End-to-end encryption prevents any intermediaries or third parties from intercepting or accessing the messages of a video conference call. This means that even if an attacker manages to intercept the message, they will be unable to read or understand it without the decryption key.
Hacking or data breaches
With end-to-end encryption, even if a communication platform experiences a data breach, the encrypted message will be unreadable to any attacker who does not have the decryption key. This protects users' sensitive information, such as meeting agendas or confidential topics, from being stolen or compromised.
User privacy & sensitive information
End-to-end encryption protects user privacy by ensuring that only the intended recipient(s) of a video conference call can read its messages. This is particularly important for companies that handle sensitive or confidential information, as it helps to maintain the privacy of clients or customers.
E2EE encryption also provides an additional layer of security for sensitive information, such as financial data or personal information, in compliance with data privacy regulations, such as GDPR or HIPAA. This is particularly important in companies where data privacy is a top concern, such as healthcare, finance, or legal services
Man-in-the-middle attacks
Man-in-the-middle (MITM) attacks are a common form of cyber-attack where an attacker intercepts communications between two parties, often to steal sensitive information. With end-to-end encryption, MITM attacks are effectively thwarted. This is because the encryption and decryption processes occur at the sender's and recipient's devices, respectively, with no intermediaries involved.

The benefits of end-to-end encrypted video conferencing
End-to-end encryption (E2EE) provides several benefits for conference calls in WebRTC:
Increased security
Confidentiality
Compliance
Trust
Flexibility
Differences between symmetric and asymmetric encryption
Symmetric and asymmetric encryption are two fundamental encryption methods used in cybersecurity. Digital Samba's video conference calls in WebRTC use asymmetric encryption, specifically end-to-end encryption, for enhanced security.
- Symmetric encryption uses a shared secret key for both encryption and decryption of data. This means that anyone who has the key can decrypt the data, making it less secure compared to asymmetric encryption.
- In contrast, asymmetric encryption, also known as public-key encryption, uses a pair of keys - a public key and a private key - for encryption and decryption, respectively. The public key is freely available and can be used by anyone to encrypt data, while the private key is kept secret and is only used by the recipient to decrypt the data. This makes asymmetric encryption more secure than symmetric encryption, as the private key is not shared with anyone else.
E2EE often combines the strengths of both symmetric and asymmetric encryption. For instance, a secure key exchange protocol like Diffie-Hellman is used to generate and share a symmetric key. This symmetric key is then used to encrypt and decrypt the actual messages, providing a balance between speed and security.
How does end-to-end encryption for conference calls work in WebRTC
End-to-end encryption (E2EE) in WebRTC is a process of securing communication between users. It involves the use of both symmetric and asymmetric encryption to provide a secure environment.
Each user in a WebRTC call has a unique public and private key pair that is generated locally on their device. When a user initiates a call, their public key is sent to the other participants, who use it to encrypt their messages. The recipient's private key is then used to decrypt the messages at their endpoints.
During a conference call, WebRTC uses symmetric encryption to encrypt the audio and video streams. A unique key is generated for each call, which is then used to encrypt and decrypt the audio and video streams. This key is never transmitted to the server, ensuring that only the participants have access to the decrypted data at their endpoints.
Forward secrecy is another feature of E2EE that provides additional security. It generates a new key for each call, making it virtually impossible for an attacker to decrypt past calls even if they obtain the encryption keys.
Overall, the implementation of E2EE in WebRTC provides a high level of security and privacy for its users. This makes it an ideal solution for businesses and organizations that require secure communication with endpoints.

Choosing the right video conferencing API provider
To successfully integrate E2EE into your video conferencing application, it's crucial to partner with a reliable video conferencing API provider, such as Digital Samba Embedded.
By selecting a provider that offers E2EE, you'll be better equipped to deliver a secure and trustworthy solution to your clients and users. Keep the following factors in mind when choosing a provider:
- Security Features: Ensure that the provider supports E2EE and other essential security features like secure authentication, access control, and secure recording.
- Scalability: Choose a provider that can scale with your application's growth, accommodating an increasing number of users and conferences without compromising performance.
- Ease of Integration: Opt for a provider with a well-documented API, making it easier for you to integrate video conferencing features into your application.
How to enable end-to-end encryption on Digital Samba
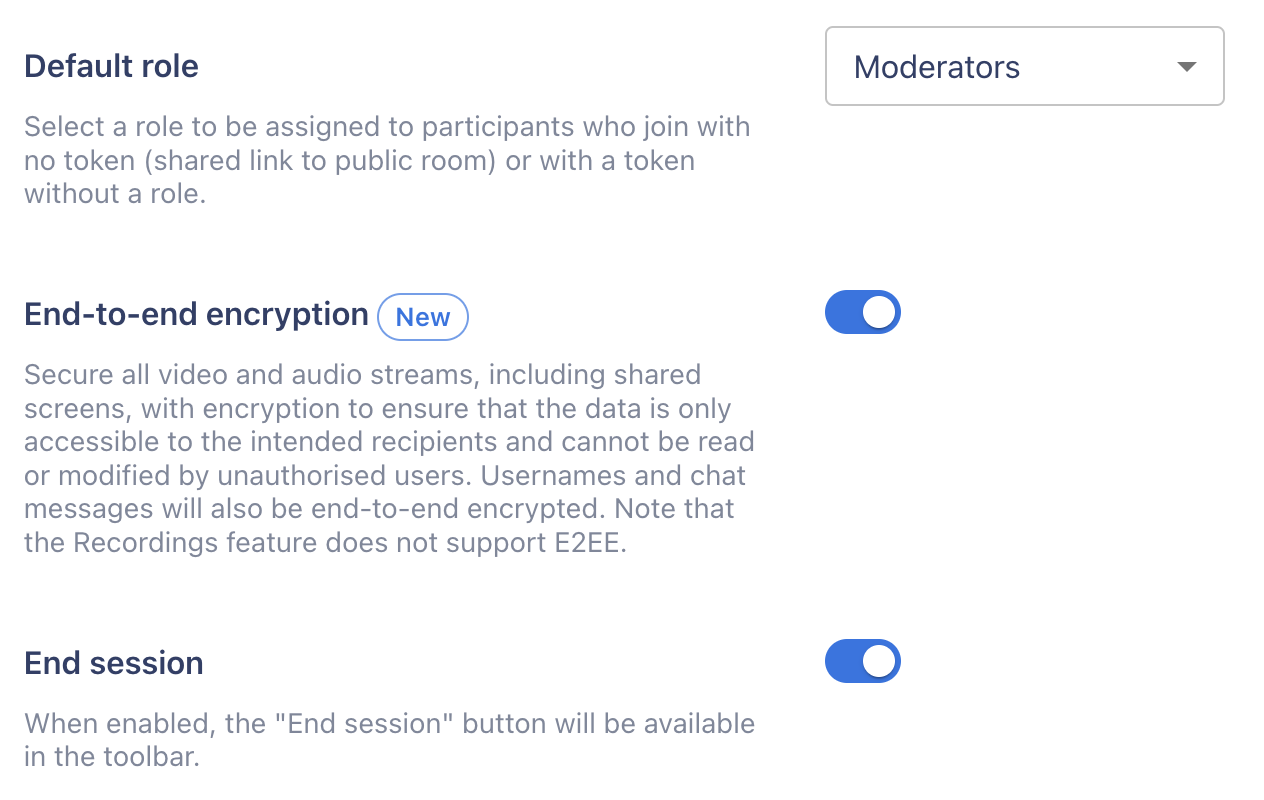
Using the dashboard
The Digital Samba dashboard provides an easy-to-use interface for managing your online meetings. In just a few clicks, you can enable end-to-end encryption (E2EE) for added security.
- Navigate to the Rooms window.
- If you’re creating a new room, click on “Create a room.”
- However, if you want to update an existing room, locate it within the rooms listed.
- Scroll down to the “End-to-end encryption” and click the toggle to enable E2EE.
Using the REST API
To enable E2EE on Digital Samba for conference calls, you can also use the platform's REST API. The API provides a simple parameter called e2ee_enabled, which takes a boolean expression as its value. Setting the value to true enables E2EE for your conference calls, ensuring that all communication is end-to-end encrypted.
To use the API, you will need to authenticate your requests using your Digital Samba API key. Once authenticated, you can make requests to create (POST) new conference calls with E2EE enabled, or update (PATCH) existing conference calls to enable or disable E2EE.
Here is an example of how to enable E2EE for a new conference call or room using the Digital Samba API:
--header "Authorization: Bearer base64(teamId:teamDeveloperKey)" \
--header "Content-Type: application/json" \
--header "Accept: application/json" \
--data '{
"topic": "standup",
"friendly_url": "my-standup",
"privacy": "public",
"external_id": "myExtID123",
"default_role": "moderator",
"roles": ["moderator"],
"e2ee_enabled": true
}'
Note that the e2ee_enabled parameter is set to true to enable end-to-end encryption for the conference call. Additionally, note that a friendly_url will be auto-generated if you do not set it, in this case, standup is used as an example.
Conclusion
For software developers, it's essential to understand the significance of end-to-end encryption and the benefits it provides to users. By integrating end-to-end encrypted video conferencing solutions into your software applications, you'll not only ensure the privacy and security of your users' communication but also increase trust in your application.
With the increasing demand for secure video conferencing solutions, partnering with a reliable video conferencing API provider like Digital Samba is necessary. By offering E2EE and other advanced security features, Digital Samba enables you to deliver a safe, reliable, and trustworthy video conferencing experience to your clients and users.
FAQs
Yes, WebRTC has built-in encryption for all data streams, including audio and video, using DTLS (Datagram Transport Layer Security) and SRTP (Secure Real-time Transport Protocol).
WebRTC is designed to be secure with mandatory encryption, secure protocols, and consent-based access to devices (like cameras and microphones). However, its security depends on implementation and usage.
Yes, it is possible to use end-to-end encryption with WebRTC, especially for data channels, by implementing additional encryption layers on top of the standard WebRTC encryption.
Encryption is necessary in WebRTC to ensure the privacy and security of the communications, protecting against eavesdropping and tampering.
WebRTC's end-to-end encryption works by encrypting media streams with keys only known to the end users, preventing intermediaries from decrypting the content. This is mainly applicable to data channels.
Security features of WebRTC include DTLS for encryption, ICE for network traversal, and consent-based access, ensuring secure, peer-to-peer connections.
Now that you're equipped with the knowledge of end-to-end encryption and its importance in video conferencing, it's time to take action. Start implementing E2EE in your video conferencing applications today and stay ahead of the competition in the ever-evolving digital landscape.
Share this
You May Also Like
These Related Stories

Digital Samba Introduces End-to-End Encryption (E2EE) for Private and Group Video Calls

GDPR Compliance in Video Meetings: What You Need To Know



